前言
Nginx (engine x) 是一个高性能的HTTP和反向代理web服务器。其特点是占有内存少,并发能力强,事实上nginx的并发能力确实在同类型的网页服务器中表现较好,使用方面。
精彩文章:
基本使用
安装
#安装
yum -y install nginx
## 日志目录
mkdir /data/log/nginx/ && chown -R nginx:nginx /data/log/nginx/
## 缓存目录
mkdir -p /var/cache/nginx/ && chown -R nginx:nginx /var/cache/nginx/配置文件
user nobody;
worker_processes auto; #nginx对外提供web服务时的worker进程数
error_log /data/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/doc/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024; #设置可由一个worker进程同时打开的最大连接数
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /data/log/nginx/access.log main buffer=32k flush=30s;
server_tokens off; #关闭在错误页面中的nginx版本数字
client_max_body_size 100m;
sendfile on; #可以让sendfile函数发挥作用。sendfile函数可以在磁盘和TCP socket之间互相拷贝数据(或任意两个文件描述符)
tcp_nopush on; #告诉nginx在一个数据包里发送所有头文件,而不一个接一个的发送
tcp_nodelay on; #不缓存数据
keepalive_timeout 65;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
#ssl 配置
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384;
ssl_ecdh_curve secp384r1;
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_session_tickets off;
ssl_stapling on;
ssl_stapling_verify on;
add_header Strict-Transport-Security "max-age=63072000; preload";
add_header X-Frame-Options SAMEORIGIN;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
#nginx缓存
fastcgi_cache_path /var/cache/nginx/ levels=1:2 keys_zone=wordpress:10m inactive=30m use_temp_path=off;
fastcgi_cache_key $request_method$scheme$host$request_uri;
fastcgi_cache_use_stale error timeout invalid_header updating http_500;
fastcgi_cache_valid 200 301 302 10h;
fastcgi_cache_valid 404 10m;
fastcgi_ignore_headers Expires Set-Cookie Vary;
#启动gzip
gzip on;
gzip_min_length 1k;
gzip_buffers 4 16k;
gzip_comp_level 7;
gzip_types
text/css
text/plain
text/javascript
application/javascript
application/json
application/x-javascript
application/xml
application/xml+rss
application/xhtml+xml
application/x-font-ttf
application/x-font-opentype
application/vnd.ms-fontobject
image/svg+xml
image/x-icon
application/rss+xml
application/atom_xml
image/jpeg
image/gif
image/png
image/icon
image/bmp
image/jpg;
gzip_vary on;
# for more information.
include /etc/nginx/conf.d/*.conf;
}
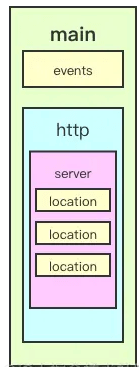
- main 全局配置,对全局生效;
- events 配置影响 Nginx 服务器与用户的网络连接;
- http 配置代理,缓存,日志定义等绝大多数功能和第三方模块的配置;
- server 配置虚拟主机的相关参数,一个 http 块中可以有多个 server 块;
- location 用于配置匹配的 uri ;
- upstream 配置后端服务器具体地址,负载均衡配置不可或缺的部分;
启动服务
systemctl enable --now nginx
# 重载配置
nginx -s reload
# 查看当前生效配置
nginx -T高级用法
泛域名强制跳转
rewrite.conf
server {
listen 80;
server_name *.chreagent.com;
return 301 https://$http_host$request_uri;
}
多级代理获取用户真实IP地址
fastcgi_temp_file_write_size 256k;
fastcgi_intercept_errors on;
#新增内容
set_real_ip_from 100.64.0.0/10; //阿里保留地址段
set_real_ip_from 101.89.27.156; //腾讯cdn
set_real_ip_from 101.89.27.209;
set_real_ip_from 101.89.32.18;
set_real_ip_from 101.89.34.154;
set_real_ip_from 101.89.34.203;
set_real_ip_from 101.89.34.214;
set_real_ip_from 101.89.34.219;
set_real_ip_from 101.89.34.223;
set_real_ip_from 101.89.34.225;
set_real_ip_from 101.89.34.226;
set_real_ip_from 101.89.34.231;
set_real_ip_from 101.89.34.239;
set_real_ip_from 101.89.34.241;
set_real_ip_from 101.89.34.243;
set_real_ip_from 101.89.34.244;
set_real_ip_from 101.89.34.55;
set_real_ip_from 101.91.24.25;
set_real_ip_from 101.91.24.37;
set_real_ip_from 116.128.128.87;
set_real_ip_from 116.128.128.91;
set_real_ip_from 116.128.128.92;
set_real_ip_from 123.151.144.103;
set_real_ip_from 123.151.144.107;
set_real_ip_from 123.151.144.114;
set_real_ip_from 123.151.144.18;
set_real_ip_from 220.194.88.144;
set_real_ip_from 220.194.88.217;
set_real_ip_from 220.194.88.252;
set_real_ip_from 220.194.88.254;
set_real_ip_from 223.166.151.125;
set_real_ip_from 58.251.121.72;
set_real_ip_from 58.251.121.81;
set_real_ip_from 58.251.121.90;
set_real_ip_from 58.251.121.93;
set_real_ip_from 59.36.117.183;
set_real_ip_from 59.36.119.251;
set_real_ip_from 59.36.120.102;
set_real_ip_from 59.36.120.233;
set_real_ip_from 59.36.95.43;
set_real_ip_from 59.36.95.48;
set_real_ip_from 61.151.164.124;
set_real_ip_from 61.151.164.190;
set_real_ip_from 61.151.164.217;
set_real_ip_from 61.151.164.218;
set_real_ip_from 61.151.164.63;
set_real_ip_from 127.0.0.1;
real_ip_header X-Forwarded-For;
real_ip_recursive on;反向代理配置示例
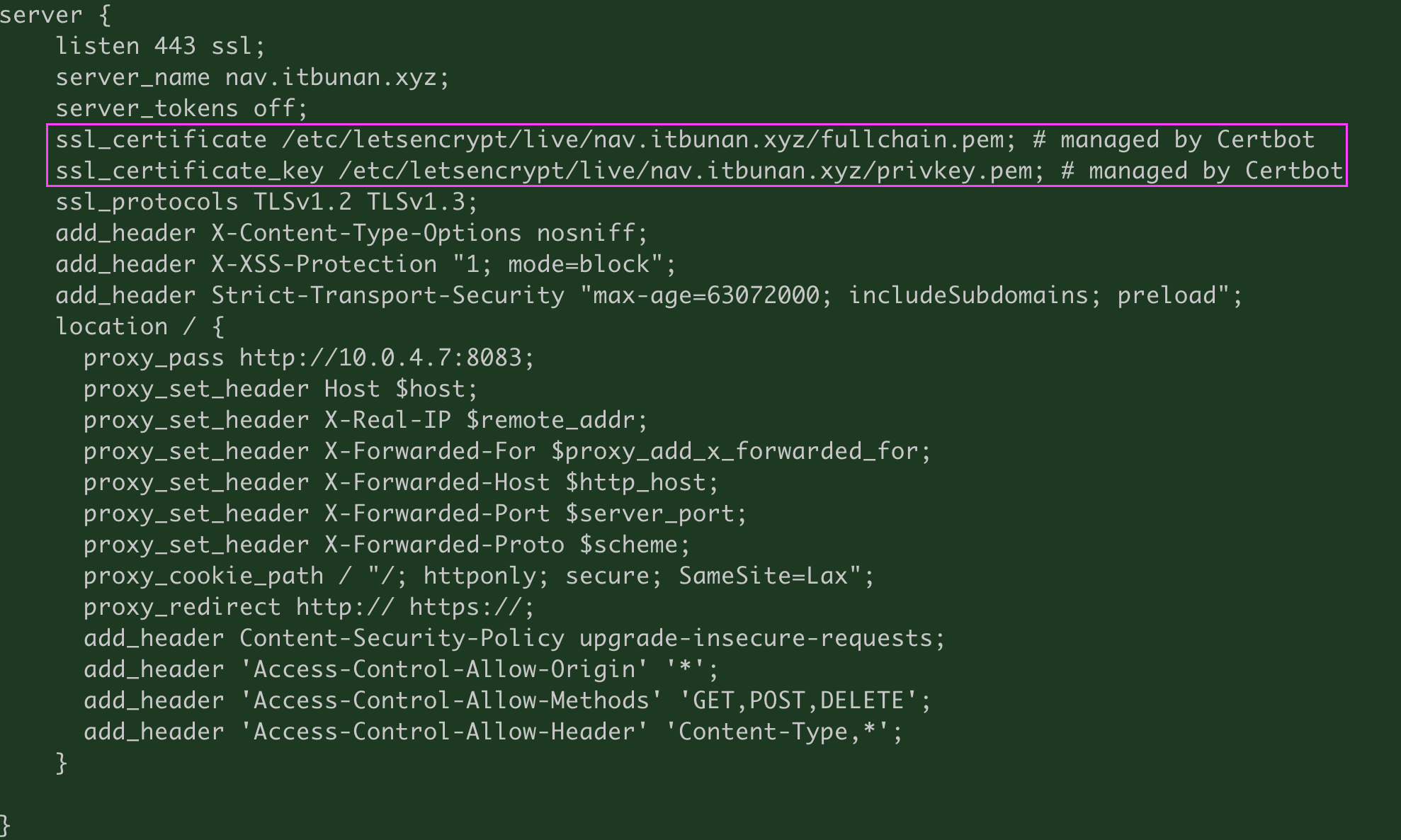
包括wss反代配置"
server {
listen 443 ssl http2;
server_name mon.itbunan.xyz;
server_tokens off;
ssl_certificate /etc/nginx/cert/mon.itbunan.xyz_bundle.crt;
ssl_certificate_key /etc/nginx/cert/mon.itbunan.xyz.key;
ssl_protocols TLSv1.2 TLSv1.3;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header Strict-Transport-Security "max-age=63072000; includeSubdomains; preload";
location /ws {
proxy_redirect off;
proxy_pass http://172.17.0.10:8008;
proxy_set_header Host $host;
proxy_set_header X-Real_IP $remote_addr;
proxy_set_header X-Forwarded-For $remote_addr:$remote_port;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection upgrade;
}
location / {
proxy_pass http://172.17.0.10:8008;
proxy_set_header Host $host;
proxy_set_header Cookie $http_cookie;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_cookie_path / "/; httponly; secure; SameSite=Lax";
proxy_redirect http:// https://;
add_header Content-Security-Policy upgrade-insecure-requests;
add_header 'Access-Control-Allow-Origin' '*';
add_header 'Access-Control-Allow-Methods' 'GET,POST,DELETE';
add_header 'Access-Control-Allow-Header' 'Content-Type,*';
}
}基于客户端IP做并发访问控制
在主配置文件内添加
# 针对原始用户 IP 地址做限制
## 用户的 IP 地址 $binary_remote_addr 作为 Key,每个 IP 地址最多有 50 个并发连接
## 你想开 几千个连接 刷死我? 超过 50 个连接,直接返回 503 错误给你,根本不处理你的请求了
limit_conn_zone $binary_remote_addr zone=TotalConnLimitZone:20m ;
limit_conn TotalConnLimitZone 50;
limit_conn_log_level notice;
## 针对原始用户 IP 地址做限制
## 用户的 IP 地址 $binary_remote_addr 作为 Key,每个 IP 地址每秒处理 10 个请求
## 你想用程序每秒几百次的刷我,没戏,再快了就不处理了,直接返回 503 错误给你
limit_req_zone $binary_remote_addr zone=ConnLimitZone:20m rate=10r/s;
#limit_req zone=ConnLimitZone burst=10 nodelay; #如果开启此条规则,burst=10的限制将会在nginx全局生效
limit_req_log_level notice;配置需要限制访问频率的server
## 具体服务器配置
server {
listen 80;
location ~ \.php$ {
## 最多 5 个排队, 由于每秒处理 10 个请求 + 5个排队,你一秒最多发送 15 个请求过来,再多就直接返回 503 错误给你了
limit_req zone=ConnLimitZone burst=5 nodelay;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
include fastcgi_params;
}
利用计划任务自动更新
#每小时58分更新一次
58 * * * * /usr/bin/sh /opt/scripts/add_blackip_for_ddos.sh > /dev/null 2>&1
#没3分钟更新一次
*/3 * * * * /usr/bin/sh /opt/scripts/add_blackip_for_ddos_per_min.sh > /dev/null 2>&1add_blackip_for_ddos.sh 脚本内容
#!/bin/bash
h_time=`env LC_ALL=en_US.en date '+%e/%b/%G:%H'`
zjlog='/data/log/nginx/itbunan_access.log'
conf='/www/server/panel/vhost/nginx/blackip.conf'
#筛选攻击IP
tail -n 5000000 $zjlog | grep "$h_time" |awk '{print $1}'| sort -k 1 | uniq -c | sort -rnk 1 | grep -v '::' > /tmp/zj_blackip.txt
cat /tmp/zj_blackip.txt | awk '{if($1>400)print "deny "$2";"}' > $confadd_blackip_for_ddos_per_min.sh 脚本内容
#!/bin/bash
h_time=`env LC_ALL=en_US.en date '+%e/%b/%G:%H'`
zjlog='/data/log/nginx/itbunan_access.log'
conf='/www/server/panel/vhost/nginx/blackip.conf'
#筛选攻击IP
tail -n 5000000 $zjlog | grep "$h_time" |awk '{print $1}'| sort -k 1 | uniq -c | sort -rnk 1 | grep -v '::' > /tmp/zj_blackip.txt
cat /tmp/zj_blackip.txt | awk '{if($1>400)print "deny "$2";"}' > $conf调试lua脚本
修改nginx配置文件
#error_log /home/wwwlogs/nginx_error.log crit;
error_log /home/wwwlogs/nginx_error.log debug;网关全站置灰
# 修改配置文件nginx.conf
http {
sub_filter '</head>' '<style type="text/css">html {-webkit-filter: grayscale(.95);}</style></head>';
sub_filter_once on;
...
}动静分离
server {
listen 80;
server_name localhost;
location / {
root e:wwwroot;
index index.html;
}
# 所有静态请求都由nginx处理,存放目录为html
location ~ .(gif|jpg|jpeg|png|bmp|swf|css|js)$ {
root e:wwwroot;
}
# 所有动态请求都转发给tomcat处理
location ~ .(jsp|do)$ {
proxy_pass http://test;
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root e:wwwroot;
}
} 防盗链
location ~* \.(gif|jpg|png|bmp)$ {
valid_referers none blocked *.ttlsa.com server_names ~\.google\. ~\.baidu\.;
if ($invalid_referer) {
return 403;
#rewrite ^/ http://www.ttlsa.com/403.jpg;
}
}FAQ
清除缓存
rm -rf /var/cache/nginx/*隐藏nginx版本号
# 修改配置文件,添加
server_tokens off;




评论 (0)